Zoom can be used to hold unlimited video conferences and virtual meetings with up to 300 participants (including screen sharing and chat options). Zoom is easy to use and highly stable - even with a large number of participants. It is a supplement to the use of Microsoft Teams, especially when many non-KIT members are involved. Please refer to the information security officer's risk and protection requirements assessment for online communication services (only accessible from the KIT network or via VPN) at KIT. At KIT, the use of recording in online communication services is regulated by recommendations for action. Our instructions follow the procedures described there.
In addition, individual licenses are available for larger participant cohorts of up to 500 or 1000 participants. Please contact us if you have a corresponding requirement.
Do you have any questions? Then please contact us by e-mail: elearning∂studium.kit.edu |
| Information on using Zoom at KIT for other events outside of teaching can be found on the Campus Services pages. |
Data protection information on Zoom at KIT
-
Data protection information on Zoom
KIT endeavors to use data protection-compliant solutions for online teaching as far as possible. Due to the currently unfeasible scaling of the existing services, the cloud-based online setting had to be used. Teachers and students are free to decide whether or not to use a cloud-based service, knowing that there are data protection concerns on the one hand and how indefinitely possible alternatives to using the cloud-based service will be available on the other.KIT ensures that non-utilization of cloud-based services is not sanctioned (e.g. by ensuring that students are not charged for missed deadlines caused by non-utilization of cloud-based courses or examinations), and thus also follows current resolutions of the Standing Conference of the Ministers of Education and Cultural Affairs.
KIT has taken extensive measures to raise the use of cloud-based services to a level that is acceptable under the circumstances caused by coronavirus. For example, the use of Zoom at KIT is based on an order data processing contract that has been adapted to meet KIT's requirements. In particular, KIT has succeeded in making the clause on the possibility of passing on personal data compliant with data protection regulations. In addition, settings and recommendations for data-saving use and for minimizing risks from an IT security perspective have been developed and implemented.For example, students can take part in the sessions without activating their microphone or webcam and do not have to provide their real name. Students are comprehensively informed about data processing via a data protection declaration. -
Criticism of Zoom
The Zoom implementation was configured by KIT for data-saving use in order to minimize risks. For example, the log-in via Facebook, feedback options to Zoom and user-related statistics are deactivated. Zoom is used by KIT via EU data centers; other data centers, e.g. in the USA or China, are deactivated.
Lecturers can only use the software on a voluntary basis after confirming that they have read the privacy policy for the use of Zoom. In addition, the KIT has made extensive settings that further increase the level of data protection of the software compared to the default settings.
The use of Zoom is currently being discussed and commented on in the press. Among other things, the privacy policy provided by Zoom itself has been criticized and there have been reports of wilful interference or vulnerabilities in the software. However, the provider reacted quickly to the information and criticism, in particular by improving the software and settings.
Statements from Zoom
The provider has recognized the great importance of data protection and information security for European users:-
In the current version of the privacy policy, the provider distinguishes between the use of the marketing pages and the use of the service. To this end, it has removed the Facebook SDK from the IOS app.
-
The provider is striving to improve transparency and implement additional security features, in particular the security vulnerabilities in the Mac client and with regard to UNC hyperlinks have been fixed: Zoom blog post: A Message to Our Users.
-
The meetings are transport-encrypted: Zoom blog post: The Facts Around Zoom Encryption for Meetings/Webinars.
-
Further adjustments have been made so that, for example, users are routed via data centers outside China: Zoom blog post: Response to Research From University of Toronto's Citizen Lab.
Encryption of the meetings
In an article, the Citizen Lab of the University of Toronto analyzed the encryption of meetings and concluded that the meetings are not suitable for particularly sensitive communication, but are suitable for usually public or semi-public events such as lectures or seminars.
Security of access data
heise Security reports that a research company has discovered access data for hundreds of thousands of Zoom accounts for sale on the Darknet. At least some of the login data is said to have been obtained by automatically trying out login data.
By using Shibboleth, we at KIT are on the safe side in the event of a specific attack on Zoom, as passwords are never stored on Zoom via this channel.
With regard to private Zoom accounts, we could advise you to follow the press and use complex passwords and different passwords for different user accounts in accordance with our practical tips on IT security, even in private.Zoom client update required (version 5.8.4)For Zoom clients up to and including version 5.8.3, a serious security vulnerability was identified by CERT-Bund(source). Therefore, after consultation with the KIT-CERT, it was decided to regularly require up-to-date versions of the Zoom client with immediate effect. Your locally installed Zoom client will indicate when an update is available. Without this update, no meeting can be started with a KIT Zoom account. The update is also required to participate in meetings conducted via KIT Zoom accounts. An update does not require any administrator authorizations and can be carried out by yourself. Alternatively, the web interface can of course be used at any time, which essentially offers an identical range of functions. -
-
Data protection and information security for users
We recommend that our users observe the following general aspects.-
Always work with an up-to-date operating system with security updates installed on your PC, laptop or smartphone.
-
Make sure that your virus protection is up to date and that you use official app stores.
-
Regularly update applications / apps, especially web browsers and meeting clients.
-
Watch out for fraudulent messages, especially links to login or download pages
-
Use the possible settings for camera / microphone use on your own system.
-
Do not pass on meeting links or meeting IDs uncontrolled, e.g. via screenshot
-
Participant names or posts in the meeting chat should be kept anonymous, meetings are a public space.
-
-
Privacy-friendly settings for Zoom through KIT
In addition, KIT has made extensive settings that further increase the level of data protection of the software compared to the default settings. Locked settings cannot be changed by lecturers, deactivated or activated settings can be changed by lecturers if necessary. The use of data centers outside the EU is blocked.-
Automatically starting the camera and enabling your own audio is blocked when joining a meeting, i.e. participants must switch on both their own audio and the camera itself.
-
Starting a recording is only possible for meeting hosts. These recordings include screen sharing as well as audio and images of speakers. Legal requirements must be taken into account when using recording functions in video conferencing services. The document in the ISB Infothek is intended to show you the legal framework and support you in using the recording functions on your own responsibility: https://www.isb.kit.edu/248.php. The instructions for teachers on the use of Zoom describe appropriate procedures.
-
Attention tracking is blocked.
-
Machine counting of participants in Zoom rooms is blocked.
-
Access to other contact data within KIT through Zoom is blocked.
-
-
Further default settings for a Zoom meeting
-
The waiting room for the meeting rooms is activated in the default settings.
-
Meetings without a password cannot be created. This is blocked.
-
File transfers in the chat are blocked and not possible.
-
-
Use of the German collaboration solution Zoom XThe KIT uses the German collaboration solution Zoom X. With Telekom as hosting partner, user data remains in Germany and is processed on servers in Germany.
-
Zoom specifies terms of use: No use of user data for AI training without consent
A section in the Zoom terms of use (§ 10.4) caused discussion as it gave the impression that user data could potentially be used to develop artificial intelligence. However, in the updated terms and conditions dated August 7, 2023, Zoom clearly states that such data may not be used for the training of AI models without the explicit consent of the user.
Further details can be found in a detailed article by Heise.
You can access Zoom with your KIT account via https://kit-lecture.zoom.us/. We recommend using the Google Chrome browser.
Please remember that you must be assigned a Zoom license once before using Zoom (further information on how to apply - page only visible in the KIT network). You must also agree to the use of Zoom at https://my.scc.kit.edu/shib/zoom.php in advance. You can then access Zoom just a few minutes after agreeing to the privacy policy.
As an alternative to using the browser, you can also install a client. If you have problems with the account and login, please refer to the Zoom FAQ.
Activation of access and confirmation of acknowledgement of the privacy policy is only necessary for meeting hosts. Participants do not need to confirm their acknowledgement. |
-
Guide to logging in via SSO in the Zoom client
-
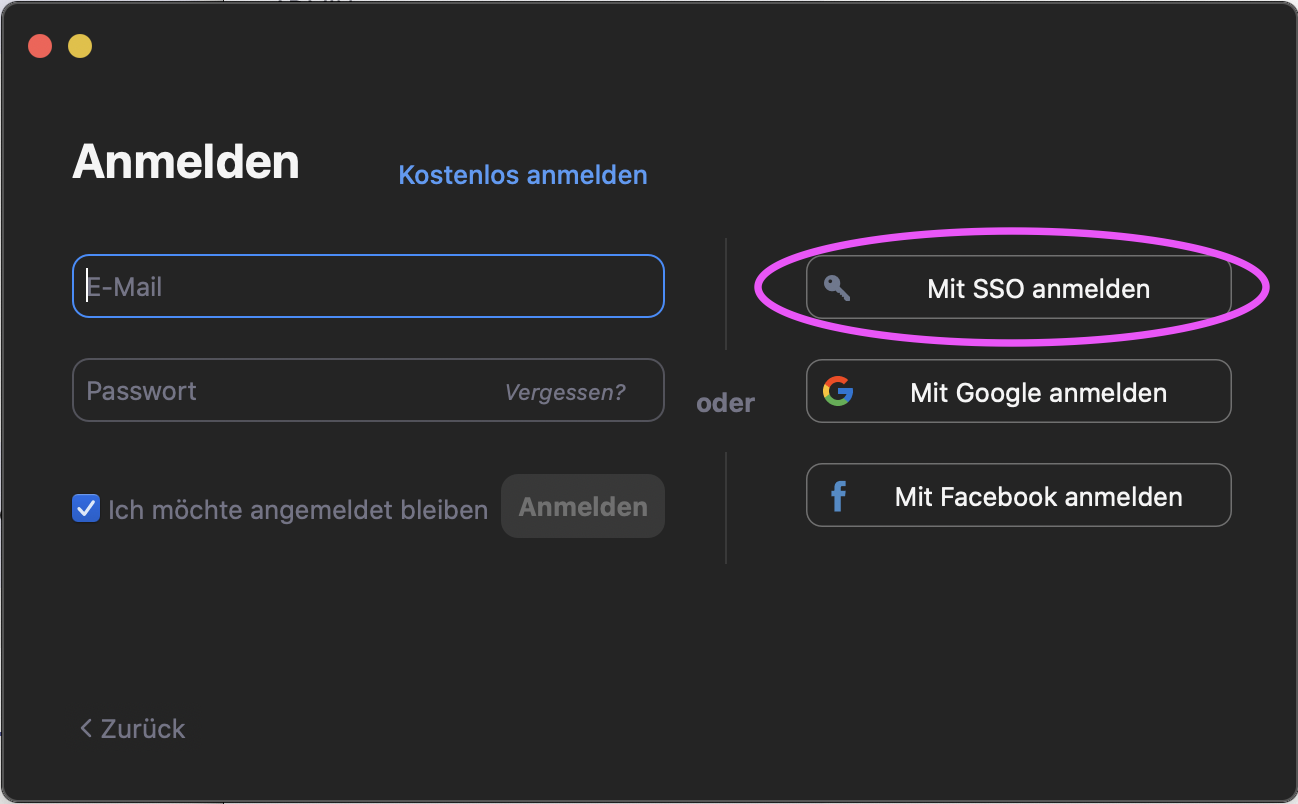
In the client, please click on "Log in with SSO" in the first dialog.
-
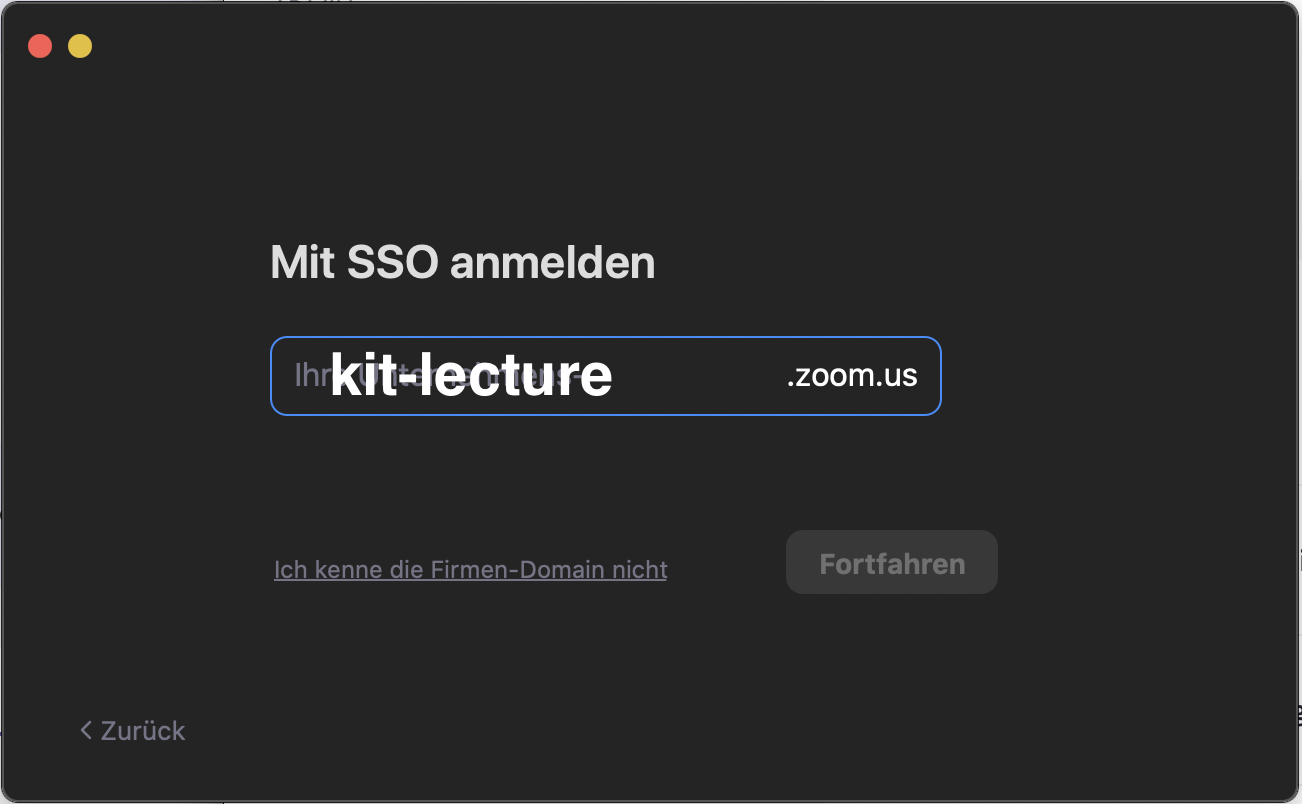
Then select "kit-lecture" as your company.
-
Then log in via KIT Shibboleth with your KIT account.
| Current clients and apps for Zoom can be found directly on the Zoom website. |